Cybersecurity in the Age of AI is no longer a niche concern—it’s the operating system of trust. Attackers now use AI to mass-personalize phishing, deepfake executive voices, and iterate payloads within hours. The good news? Teams that practice Cybersecurity in the Age of AI as a repeatable playbook—identity first, least privilege, explainable detection, human verification, and tested recovery—win more often, with less drama.
This expanded executive-friendly guide turns Cybersecurity in the Age of AI into practical steps, dashboards, and drills your team can run in 30 days and sustain quarter after quarter. Educational only—consult your legal, compliance, and security leaders for decisions.
Table of Contents
- Why Cybersecurity in the Age of AI changes the threat model
- 7 defenses that work for Cybersecurity in the Age of AI
- 30-day implementation checklist (sprint plan)
- Voice-fraud & deepfake playbooks that actually work
- AI vs. traditional threats (what’s new)
- What to measure and report to leadership
- Mini case studies: wins, near-misses, and lessons
- Governance: mapping controls to frameworks
- Lean budget blueprint for Cybersecurity in the Age of AI
- Common pitfalls (and quick fixes)
- FAQs
- Conclusion & next steps
- References
Why Cybersecurity in the Age of AI changes the threat model
Generative tools produce tailored spear-phishing at scale, clone executive voices for wire-fraud, and help criminals test payloads against defenses. Meanwhile, defenders can use anomaly detection on sign-ins, data movement, and endpoint behavior. Cybersecurity in the Age of AI therefore blends time-tested controls (identity, least privilege, logging) with AI-assisted detection and human verification steps.
Two realities define this era: (1) attacks are cheaper to launch and more convincing; (2) the fundamentals still decide outcomes. If identity is weak, backups are untested, or cloud roles are over-permitted, AI makes failure faster. If those fundamentals are strong, AI helps you spot trouble sooner and recover faster. In short, Cybersecurity in the Age of AI is about amplifying fundamentals with automation—not replacing judgment.
தமிழில் ஒரு நினைவூட்டல்: “அவசரம்—சந்தேகத்துடன் வரும் பணப்பரிவர்த்தனை கோரிக்கைகள்—எப்போதும் ‘அறிந்த எண்’ வழியே மீள் உறுதிசெய்க.” இந்த எளிய நடைமுறை தான் Cybersecurity in the Age of AI காலத்தில் பல மோசடிகளை நிறுத்துகிறது.
7 defenses that work for Cybersecurity in the Age of AI
- MFA everywhere (prefer phishing-resistant).
What it is: Require a second factor on email, VPN, admin consoles, payroll, and cloud control planes. Prefer FIDO2/security keys or platform passkeys for admins.
Quick wins: Enforce MFA tenant-wide; block SMS for admins; require keys for finance/HR.
Metric: % of active users with MFA; separate % for privileged roles.
Why it matters for Cybersecurity in the Age of AI: AI-crafted phishing increases click-through; phishing-resistant MFA removes the password replay path. - Zero Trust access.
What it is: Never trust, always verify: user identity, device health, and request context on every access. Segment networks; restrict lateral movement; apply least privilege to cloud/IAM roles.
Quick wins: Conditional access by device health and geolocation; remove standing admin; require just-in-time elevation.
Metric: # of high-risk sign-ins blocked; # of stale privileges removed.
Why it matters: Cybersecurity in the Age of AI means adversaries move fast; segmentation turns blast radius into paper cuts. - AI-assisted threat detection.
What it is: Behavioral analytics and anomaly detection across sign-ins, endpoint events, and data exfiltration.
Quick wins: Turn on baseline anomaly policies; tune alerts to reduce noise; set automatic containment for known bad patterns.
Metric: Mean time to detect (MTTD) and mean time to respond (MTTR).
Tip: Favor tools that explain “why” an alert triggered so analysts can act with confidence. - Employee awareness & simulations.
What it is: Quarterly phishing simulations and just-in-time nudges; a simple “pause & verify” culture for payment changes and sensitive data requests.
Quick wins: Teach deepfake tells: unusual urgency, payment redirects, voice that avoids live Q&A; require callback to a known number for finance approvals.
Metric: Simulation pass rate; # of reported phish; % of staff completing micro-courses.
Why it matters: Humans remain the adaptive core of Cybersecurity in the Age of AI. - Data protection & backups.
What it is: Classify sensitive data, enable DLP (email/storage), and keep immutable/offline backups with tested restores.
Quick wins: Tag customer and financial data; block risky sharing; test a restore of one critical system monthly.
Metric: Time to restore (RTO) from last immutable backup; % of protected mailboxes/drives. - Cloud security monitoring.
What it is: Centralize logs (cloud + SaaS), alert on risky IAM changes, and codify guardrails in infrastructure-as-code.
Quick wins: Remove public buckets; enforce TLS; prevent default-open security groups; enable object-lock/immutability where supported.
Metric: # of misconfigurations auto-remediated; % of resources covered by guardrails. - Incident response you can actually run.
What it is: Clear ownership, isolation steps, comms plan, and decision thresholds. Pre-stage playbooks for ransomware, account takeover, vendor compromise, and deepfake fraud.
Quick wins: One-page “wire-fraud callback” policy; out-of-band comms; endpoint isolation script; legal/PR contacts on file.
Metric: Tabletop completion; lessons-learned issues closed; time to contain during drills.


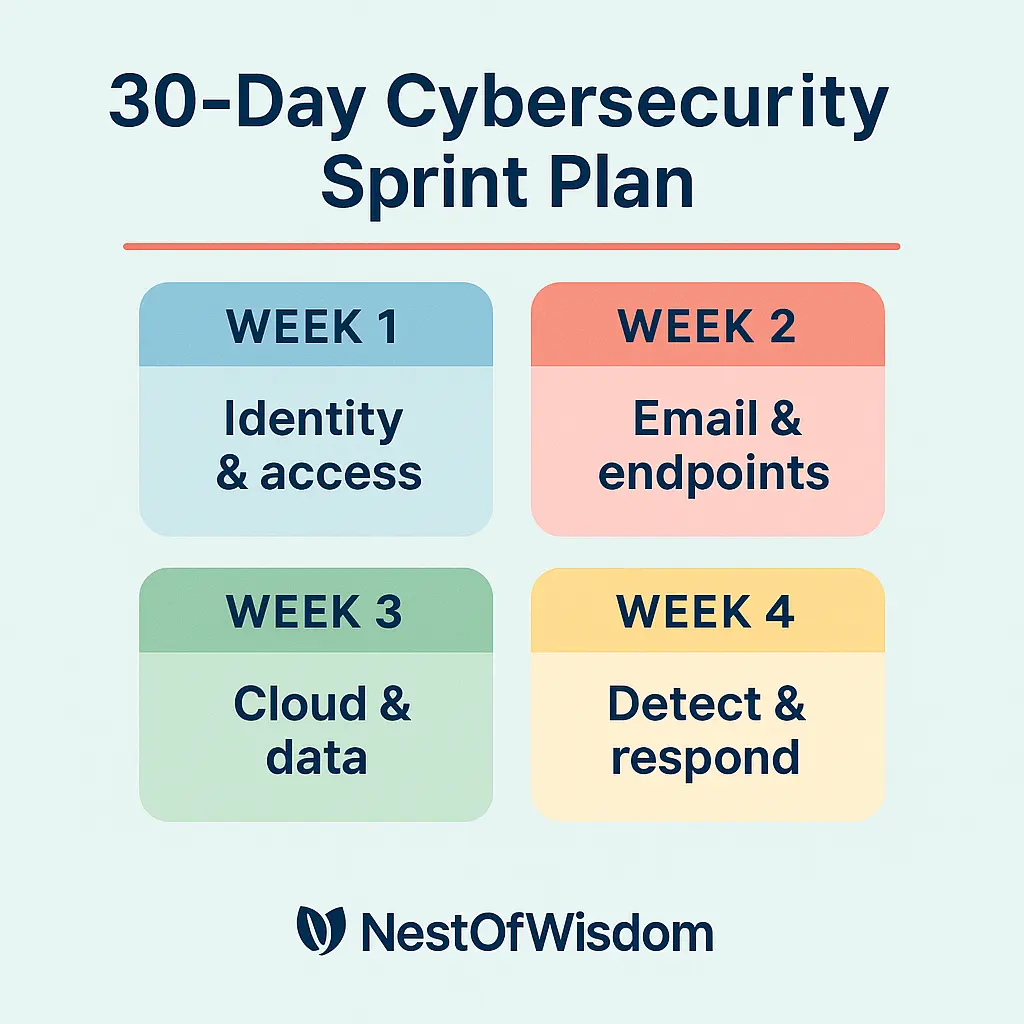
30-day implementation checklist (sprint plan)
Use this plan to operationalize Cybersecurity in the Age of AI without boiling the ocean. Re-run it quarterly and report results in one page.
Week 1 — Identity & access
- Enforce MFA for all users; require phishing-resistant keys for admins, finance, and HR.
- Turn on conditional access by device health, location, and risk score.
- Audit shared mailboxes and service accounts; remove unused access and stale app passwords.
Week 2 — Email & endpoints
- Enable advanced phishing protection and align DMARC/DKIM/SPF.
- Roll out endpoint protection with behavioral detection (EDR); block unsigned macros and risky scripts.
- Run one targeted phishing simulation and a 10-minute micro-course on deepfakes.
Week 3 — Cloud & data
- Baseline S3/Blob permissions; remove public buckets and default-open security groups.
- Set DLP rules for customer data; encrypt at rest and in transit.
- Enable immutable/offline backups and test a restore of one critical system.
Week 4 — Detect & respond
- Centralize logs (cloud + SaaS); add alerts for admin-role changes and mass downloads.
- Tabletop a voice-deepfake wire-transfer attempt; refine the escalation tree.
- Publish a one-page policy on verification callbacks for payment and bank-detail changes.

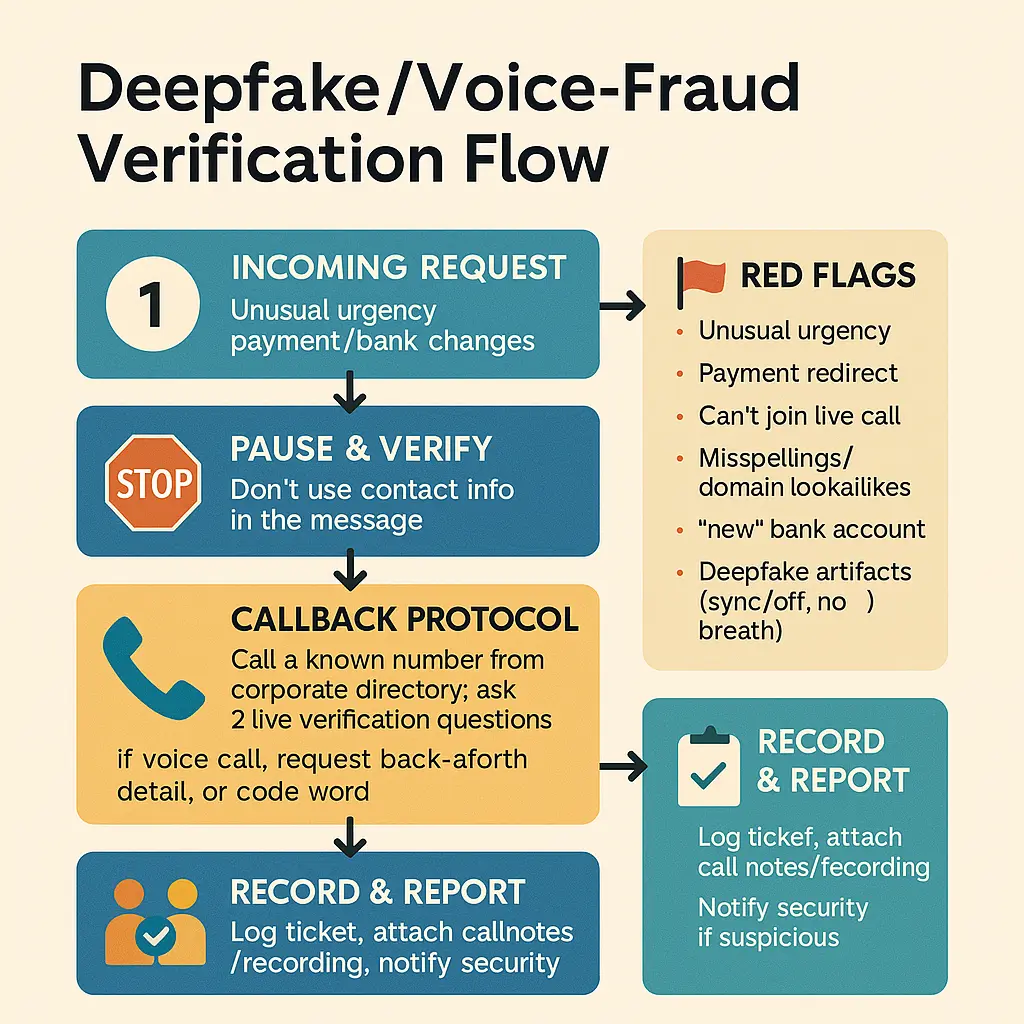
Voice-fraud & deepfake playbooks that actually work
Wire-fraud via deepfake audio is rising. The fix is surprisingly human: Cybersecurity in the Age of AI relies on a “verify-out-of-band” habit you can rehearse.
- Trigger — Any urgent payment or bank-detail change request (email, chat, or voice).
- Pause — No action until verified. Log a ticket.
- Verify — Callback to a known number from the internal directory (never the number in the message). Ask a shared-secret question.
- Two-person rule — Require a second approver for high-risk payments.
- Record — Capture verification notes in ERP/finance system.

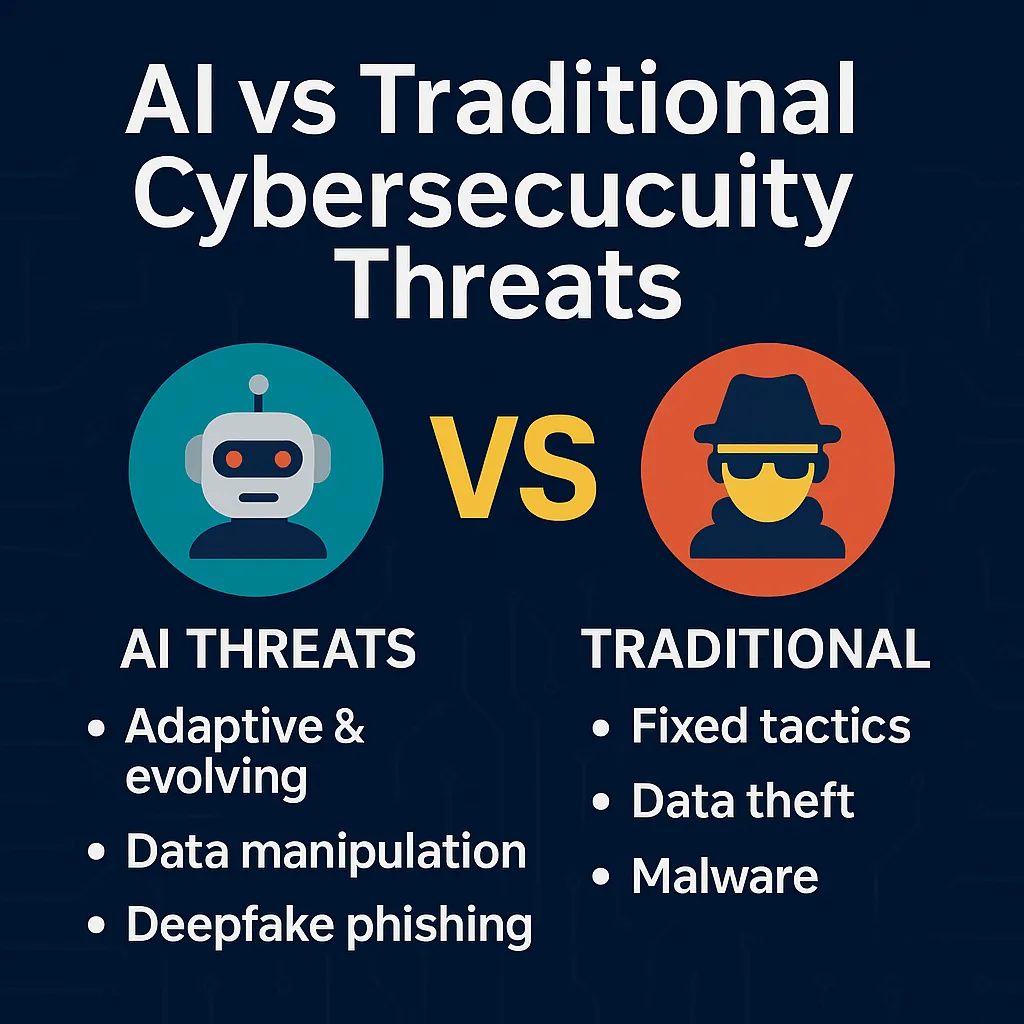
AI vs. traditional threats (what’s new)
Here’s how Cybersecurity in the Age of AI changes the landscape compared with legacy attacks. The goal isn’t panic—it’s clarity about controls that address both.

What to do differently: raise the bar on identity (passkeys), automate config guardrails, add explainable analytics, and adopt verification habits in finance and HR. That is Cybersecurity in the Age of AI in one sentence.
What to measure and report to leadership
- Identity hardening: % of users on MFA; % of privileged roles on phishing-resistant keys.
- Detection & response: Mean time to detect (MTTD) and mean time to respond (MTTR).
- Email resilience: Phishing-simulation pass rate; # of reported phish vs. clicked.
- Cloud posture: # of misconfigurations auto-remediated; % resources behind guardrails.
- Recovery readiness: Time to restore from last immutable backup; drill frequency and success rate.
Report simple trend lines monthly. Leaders don’t need tool names; they need evidence that risk is trending down and recovery is proven. Tie each chart back to how it strengthens Cybersecurity in the Age of AI outcomes customers care about (availability, integrity, confidentiality).
Mini case studies: wins, near-misses, and lessons
Case 1 — The $250K wire that never left
An urgent “CEO” call asked finance to change beneficiary details within 10 minutes. The analyst applied the verification flow, called the CEO’s known number, and discovered a deepfake. Lesson: Cybersecurity in the Age of AI succeeds when teams feel safe to pause, verify, and escalate—even under pressure.
Case 2 — The “harmless” public bucket
A marketing dataset was left open “just for a week” to test a tool. Cloud guardrails flagged it and auto-closed exposure. Lesson: Infrastructure-as-code guardrails make Cybersecurity in the Age of AI boring in the best way—safe by default.
Case 3 — Ransomware drill, real recovery
IT practiced a monthly restore from an immutable backup. When a real incident hit, recovery SLAs held. Lesson: tested backups are oxygen. Without them, Cybersecurity in the Age of AI is only as strong as your last good copy.
Governance: mapping controls to frameworks
Keep a one-page governance register mapping your controls to known references. This proves diligence and helps new hires see how Cybersecurity in the Age of AI fits into the bigger picture.
- NIST AI RMF: risk identification, measurement, governance, and continuous improvement.
- Zero Trust: verify explicitly, use least privilege, assume breach.
- OWASP Top 10: apply to apps and APIs (auth, injection, secrets, logging).
Internal reading to operationalize: AI Copilots at Work, Green Tech in the Cloud, MIT Generative AI ROI Report, Cloud Computing Benefits for Businesses. These resources connect productivity and platform choices back to Cybersecurity in the Age of AI.
Lean budget blueprint for Cybersecurity in the Age of AI
Small teams can make measurable progress with a tight spend if they prioritize:
- Identity first (30–40% of budget): MFA, passkeys/security keys, SSO/IdP consolidation.
- Email & endpoint (25–30%): advanced phishing protection + EDR with behavioral analytics.
- Cloud guardrails (15–20%): CSPM basics, IaC policies, log centralization for core services.
- Backups (10–15%): immutable/offline copies + monthly restore drills.
- Awareness & simulations (5–10%): micro-courses, seasonal drills, deepfake table-tops.
Bundle where possible to reduce vendor sprawl. Track MTTD/MTTR and recovery tests to prove that spend improves Cybersecurity in the Age of AI outcomes, not just tooling lists.
Common pitfalls (and quick fixes)
- Only buying tools. Fix identity, patching, and backups first; then add AI analytics.
- Ignoring the human layer. Simulate attacks and coach “pause & verify” for finance, HR, and executive assistants.
- Over-permissioned cloud roles. Audit IAM monthly; apply least privilege and time-bound elevation.
- No immutable backups. Keep offline/immutable copies; test restores quarterly.
- Unclear IR ownership. Assign decision-makers and out-of-band comms before an incident.
FAQs
1) Is AI detection enough to stop attacks?
No single tool is sufficient. Combine MFA, Zero Trust, user training, logging, and tested response. That layered approach is the core of Cybersecurity in the Age of AI.
2) Are passkeys/security keys worth it for small teams?
Yes. Phishing-resistant MFA dramatically cuts account-takeover risk, especially for admins and finance roles. It’s one of the highest-leverage investments in Cybersecurity in the Age of AI.
3) What’s the simplest way to counter deepfake scams?
Use verification callbacks to known numbers, require two-person approval for urgent payments, and train staff to escalate suspicious requests. These habits anchor Cybersecurity in the Age of AI in real workflows.
4) How do we choose tools without overspending?
Prefer platforms that cover identity, email, endpoint, and cloud logs with explainable alerts. Pilot with a small scope, measure MTTD/MTTR, then expand—an approach aligned with Cybersecurity in the Age of AI maturity.
5) How do we show compliance progress?
Map your controls to known frameworks (Zero Trust, NIST AI RMF). Keep a one-page register of policies, drills, and metrics; review quarterly. This makes Cybersecurity in the Age of AI visible to auditors and executives.
Conclusion & next steps
Cybersecurity in the Age of AI is achievable with a focused playbook. Start with identity, harden email and endpoints, tune cloud guardrails, and test incident response. Repeat quarterly, measure a few outcomes, and keep training human defenders—the most adaptable layer you have. With steady habits and clear dashboards, Cybersecurity in the Age of AI becomes a competitive advantage customers can feel.
Explore more on our site: AI Copilots at Work, Green Tech in the Cloud, MIT Generative AI ROI Report, Cloud Computing Benefits for Businesses.
References
- CISA — Phishing, ransomware, and incident-response guidance
- NIST — Zero Trust architecture resources
- NCSC (UK) — Zero Trust collection
- OWASP — Top 10 application risks
Nest of Wisdom Insights is a dedicated editorial team focused on sharing timeless wisdom, natural healing remedies, spiritual practices, and practical life strategies. Our mission is to empower readers with trustworthy, well-researched guidance rooted in both Tamil culture and modern science.
இயற்கை வாழ்வு மற்றும் ஆன்மிகம் சார்ந்த அறிவு அனைவருக்கும் பயனளிக்க வேண்டும் என்பதே எங்கள் நோக்கம்.
- Nest of Wisdom Authorhttps://nestofwisdom.com/author/varakulangmail-com/
- Nest of Wisdom Authorhttps://nestofwisdom.com/author/varakulangmail-com/
- Nest of Wisdom Authorhttps://nestofwisdom.com/author/varakulangmail-com/
- Nest of Wisdom Authorhttps://nestofwisdom.com/author/varakulangmail-com/
Related posts
Today's pick
Recent Posts
- Internal Linking Strategy for Blogs: A Practical, Human-Centered Playbook
- AI in the Automotive Industry: A Practical, Human-Centered Guide
- Cloud Tools for Small Businesses and Freelancers: The Complete Guide
- Generative AI in Business: Real-World Use Cases, Benefits & Risks
- 7 Life-Changing Daily Habits for Weight Loss Without Dieting